Best VPN Protocols
Ready to use a VPN service? Then you need to learn some info about VPN protocols to make sure your VPN provider gives you the top online protection and security. Namely, what are the best VPN protocols (and is it the same as the fastest VPN protocols) and what is IKEv2, OpenVPN®, TCP, UDP, WireGuard®, L2TP, IPsec? Let’s dive right in!
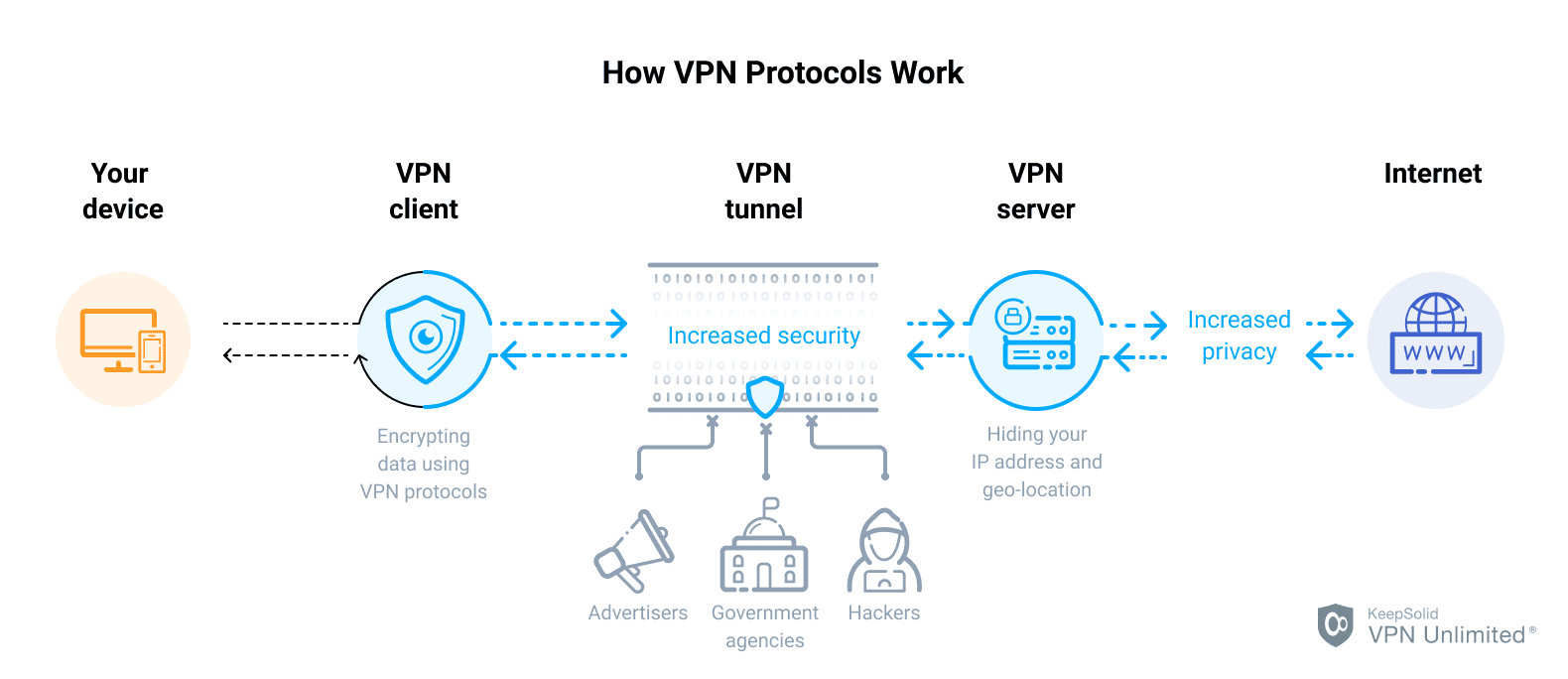
Let’s start with the definition. A VPN protocol refers to a set of processes that VPN providers use to ensure you get a secure and fast connection to VPN servers and back. Simply stated, it is a method by which your device connects to a VPN server.
VPN Unlimited offers a variety of protocols, each with its unique capabilities and strengths. Consider what protocols your device supports and whether any of them are blocked by your network. Then, choose the one with a balance between security, online freedom, and speed that is best suited to your needs.
By default, VPN Unlimited uses the optimal VPN protocol that’s best for your network, but you can also configure your app to use other protocols. Just choose the one you would like to try in your VPN settings. Here is a chart with all possible options that are currently available:
| Platform | Available Protocols | |
|---|---|---|
| Android | IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP, WireGuard® | |
| Windows Standalone version | IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP, WireGuard® | |
| Windows Store version | IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP, WireGuard® | |
| Windows Mobile | L2TP | |
| iOS | IPSec (for older OS versions), IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP, WireGuard® | |
| macOS | IPSec (for older OS versions), IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP, WireGuard® | |
| Linux | IKEv2, OpenVPN®, KeepSolid Wise TCP/UDP | |
| Google Chrome, Mozilla Firefox, Opera, Edge | TLS encryption |
Get VPN Unlimited and use the best VPN protocols!
The Best VPN Protocol
So, considering the abundance of VPN protocols to choose from, what is the best one? This is the tricky part - there is no such thing as the universally best VPN protocol for all occasions. Which will end up the best VPN protocol for you depends on and what you do on the internet and why you need a VPN protocol. Gamer’s VPN needs will differ from those of a cinephile, which will differ from a remote worker’s or a traveler’s.
You don’t need to settle for just using a single VPN protocol. Continuing our example, if you’re an online gamer or just watching favorite live sports then connection speed is more important for you now. IKEv2 will be the best VPN protocol for this case. And if your goal is to keep your sensitive personal data extremely secure, go for OpenVPN®. Or you could go for WireGuard® VPN protocol for the best mix of speed and protection!
The fastest VPN protocols
As we’ve mentioned earlier, Wireguard is widely considered to be the fastest VPN protocol. It certainly is one of the newest ones, which means it utilizes up-to-date technologies to offer quick connection (and a sweet bonus for mobile devices - an improved battery life). IPsec and IKEv2 protocols are also considered fast VPN protocols, although in them it comes at the expense of security.
The most secure VPN protocols
Although somewhat debatable, many security experts recommend OpenVPN when it comes to data and traffic protection. Similar to, say, WireGuard, it uses 256-bit data encryption by default. But it also offers other protocols, including Triple Data Encryption Standard (3DES), CAST-128, Blowfish, and AES (Advanced Encryption Standard). In VPN Unlimited, we use the most secure protocol option AES-256 bit.
The easiest VPN protocol to set up
The best thing about VPN services like VPN Unlimited is that we’ve already done all the heavy lifting for you! We have already set up and configured all available VPN protocols so that you don’t have to worry about that part. Simply pick a protocol from the list in the settings and it will work out of the box. No tweaking or tinkering required!
There might not be a single best VPN protocol, but there sure is the best VPN - VPN Unlimited!
Best VPN Protocol Encryption
According to Edward Snowden, “properly implemented strong crypto systems are one of the few things that you can rely on.” This means that the encryption does work.
The encryption itself is a process of encoding messages or information that makes sense in such a way that only authorized parties can read it. For interceptors, the encoded message looks like gibberish. The commonly used encryption methods are 128-bit and 256-bit (in a key length). They are considered to be of military level, and are widely used by the US government to protect their “sensitive” data.
Generally, 128-bit encryption is uncrackable through brute force, and it is believed to be so for another hundred years or so. However, taking into account the scale of resources that the NSA seems to have thrown at cracking encryption, it is a good practice to upgrade cipher key lengths to 256-bit. This key would require twice as much computational power to break it as a 128-bit one.
That’s why VPN Unlimited uses the 256-bit encryption algorithm with all our VPN protocols. This ensures the best security and performance.
Best VPN Protocol Ciphers
A cipher is a mechanical operation, known as an algorithm, and used for performing the encryption or decryption of a certain information, such as video files, images, or simple messages. The encrypting/decrypting procedure depends on the key, a piece of auxiliary information which changes the detailed operation of the algorithm.
VPN Unlimited uses AES cipher that, today, is generally considered to be the most secure cipher for VPN use, as well as for all other applications that now exist. It is highly efficient on a wide variety of hardware, from smartphones and tablets, to high-performance computers.
Combining the AES cipher with the 256-bit key, VPN Unlimited protects our users and grants them the security of web traffic and browsing.
TCP vs UDP - Which One is Best for VPN
The TCP port provides reliable, ordered, and time-tested end-to-end delivery of a stream of information packets online. It is one of the most widely-used protocols in digital network communications, and one of the main parts of the internet protocol suite, commonly known as TCP/IP. Applications that require a reliable data stream service are recommended to use this connection-oriented protocol.
The UDP is a simple protocol for network applications based on Internet Protocol (IP). UDP is the main alternative to TCP and one of the oldest network protocols. UDP is an ideal protocol for network applications in which perceived latency is critical, such as gaming, voice, and video communications. The protocol permits individual packets to be dropped and UDP packets to be received in a different order than that in which they were sent, allowing for better performance.
Start using our secure VPN right away!
Download VPN Unlimited now and get a 7-day free trial and unique lifetime subscription plan, during which you can check all VPN protocols!
“OpenVPN” is a registered trademark of OpenVPN Inc. “WireGuard” is a registered trademark of Jason A. Donenfeld.