What is IKE and IKEv2 VPN protocol?
Internet Key Exchange or IKE is an IPSec-based tunneling protocol that provides a secure VPN communication channel and defines automatic means of negotiation and authentication for IPSec security associations in a protected manner. The first version of this VPN protocol (IKEv1) was introduced in 1998, and the second (IKEv2) came out 7 years later. There are several differences between IKEv1 and IKEv2, not the least of which is the reduced bandwidth requirements of IKEv2.
Benefits of IKEv2 VPN Protocol
Why use IKEv2:
- 256-bit data encryption
- Implements IPSec for security
- Stable and consistent connection
- MOBIKE support ensures better speed
Security. IKEv2 employs server certificate authentication, which means it won’t perform any actions until it determines the requestor's identity. This derails most of the man-in-the-middle and DoS attack attempts.
Reliability. In the first version of the protocol, if you tried to switch to a different internet connection, e.g. from WiFi to mobile internet, with VPN on, it would disrupt the VPN connection and would require a reconnection. This has certain undesirable consequences like performance drops and a previous IP address getting changed.
Thanks to the reliability measures implemented in IKEv2, this issue has been fixed. Moreover, IKEv2 implements a MOBIKE technology, which allows it to be used by mobile and multi-homed users. It is also one of the few protocols that support Blackberry devices.
Speed. Well-minded architecture and effective message exchange system in IKEv2 allow for better performance. Also, its connection speed is significantly higher, not least because of a built-in NAT traversal which makes passing through firewalls and establishing a connection much faster.
Features and Technicalities of IKEv2 VPN Protocol
The goal of IKE is to independently produce the same symmetric key for the communicating parties. This key serves to encrypt and decrypt the regular IP packets, used to transfer data between VPN peers. IKE builds a VPN tunnel by authenticating both sides and reaching an agreement on methods of encryption and integrity. The outcome of an IKE negotiation is a Security Association (SA).
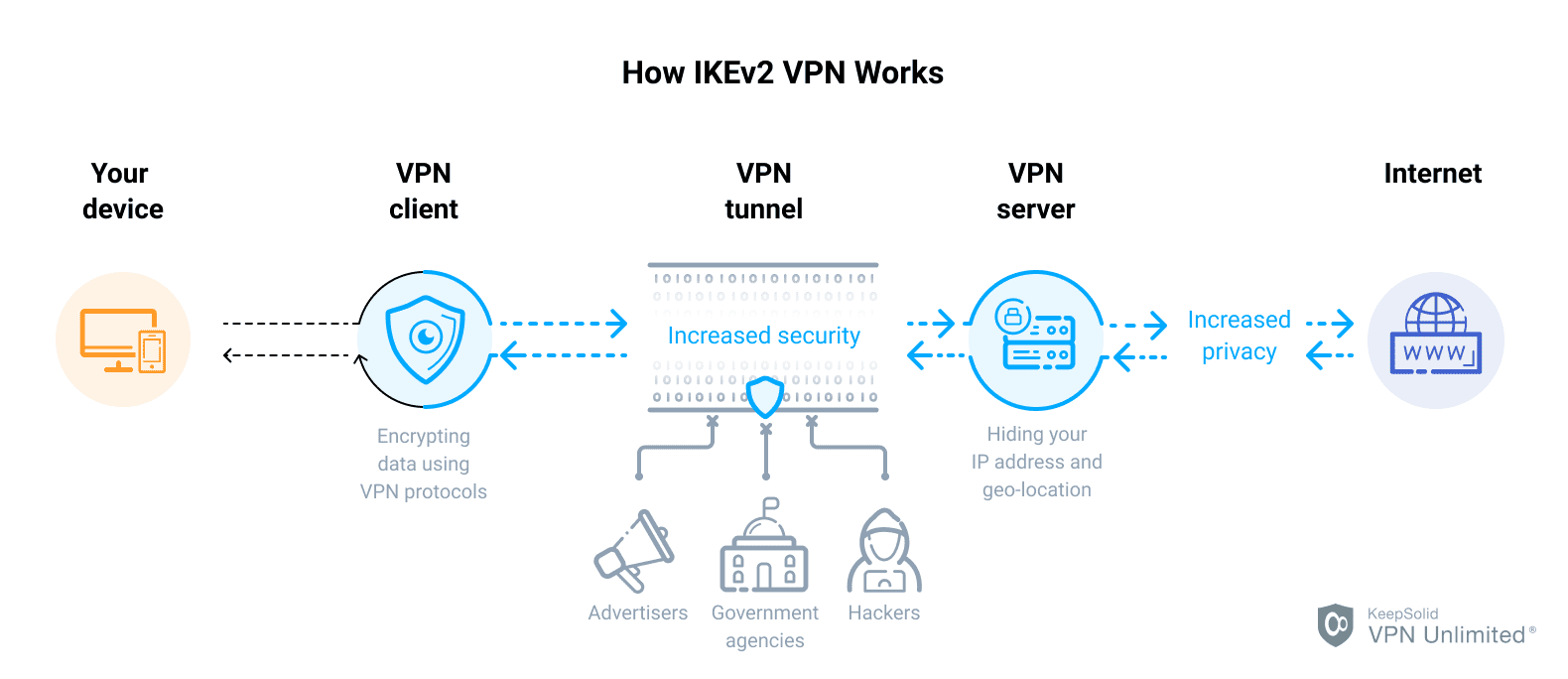
IKE is based on the underlying security protocols, such as the Internet Security Association and Key Management Protocol (ISAKMP), A Versatile Secure Key Exchange Mechanism for internet (SKEME), and the Oakley Key Determination Protocol. ISAKMP specifies a framework for authentication and key exchange but does not define them. SKEME describes a versatile key exchange technique, which provides a quick key refreshment. Oakley allows authenticated parties to exchange keying material across an insecure connection using the Diffie–Hellman key exchange algorithm. This method provides perfect forward secrecy for keys, identity protection, and authentication.
The IKE protocol uses UDP port 500 that is perfect for network applications in which perceived latency is critical, such as gaming, voice, and video communications. Moreover, the protocol does not involve the overhead, associated with Point-to-Point protocols (PPP). This makes IKE faster than PPTP and L2TP. While supporting AES and Camellia ciphers with a key length of 256 bits, IKE is considered to be a very secure protocol.
Ready to get started with the IKEv2 client?
Check our detailed guide on how to configure the IKEv2 connection on your device!
IKEv2 VS IKE - Technical Differences
IKEv2 introduced many improvements and is undeniably better than IKEv1. The benefits of IKEv2 over IKEv1 are as follows:
- To establish a VPN tunnel, IKEv2 requires fewer messages exchanged between tunnel endpoints (four messages for IKEv2 VS IKEv1’s six)
- IKEv2 comes equipped with NAT-T functionality that grants better compatibility between vendors
- IKEv2 supports Extensible Authentication Protocol (EAP)
- IKEv2 offers better stability thanks to the Keep Alive option
- For an even more stable connection, IKEv2 supports MOBIKE, a.k.a Mobility and Multi-homing protocol. It allows IKEv2 to maintain a VPN session when a user switches IP addresses, without having to re-establish the connection. The lack of this feature was a significant security issue in IKEv1 that could result in a data leak. If, for instance, a user hopped from an office WiFi to an Ethernet connection, this could interrupt the VPN session
- Security Associations in IKEv2, a.k.a Child SAs, can be independently created, deleted, and modified, at any time during the VPN tunnel’s life
- IKEv2 requires fewer Security Associations per tunnel, which reduces the required bandwidth
- IKEv2 defines all message types as Request and Response pairs, making the protocol more reliable
- IKEv2 supports Asymmetric authentication
The best VPN with IKEv2
IKEv2 VPN Protocol Pros and Cons
Pros
- Faster than PPTP and L2TP
- Supports high-grade encryption methods
- Stable when changing networks and to re-establishing a VPN connection when it was temporarily lost
- Offers an enhanced mobile support
- Easy to set up
Cons
- Uses UDP port 500 that can cause blocks from some firewalls
- Not easy to implement at the server-end
VPN Unlimited and IKEv2
IKEv2 protocol is available in VPN Unlimited for:
- Android
- Windows
- iOS
- macOS
- Linux
FAQ About VPN and IKEv2 Protocol
How do I connect to IKEv2 in VPN Unlimited?
What port is IKEv2?
Is IKEv2 VPN secure?
Can IKEv2 be hacked?
Something’s not working, where can I find help?
Download VPN Unlimited for free and get IKEv2 today!
Grab your 7-day free trial and check out how the IKEv2 protocol works for your online privacy. You can find this protocol, along with other available VPN protocols, in VPN Unlimited settings.