Can a VPN Be Hacked or Compromised? – In Light of Data Breaches

Updated on July 13, 2021: From now on, traffic filtering, malware protection, and suspicious DNS activity blocking are available as a part of the separate DNS Firewall app.
Data breaches are all the rage nowadays. Infamous Equifax data breach, less known Capital One hack that affected 140,000 Social Security numbers and 80,000 bank account numbers, Facebook / Cambridge Analytica scandal, and the most recent US – South Korea leak of over 1 million credit card data.
It’s no wonder people are looking for ways to protect their sensitive information, and some find it in VPNs. VPN, a.k.a. Virtual Private Network, is a wonderful piece of technology. It grants lay netizens nigh-corporate-level data protection, privacy, anonymity, and internet freedom. But how secure is it? Can a VPN be compromised? Can the VPN-encrypted data be hacked? Let’s find out!
How Does a VPN Work and Should it Protect from Hackers?
Before we figure out whether a VPN can be hacked, it’s important to understand how it works in the first place and if it’s even intended to protect from hackers. Let’s go over the basics fast and see how your internet connection is established.
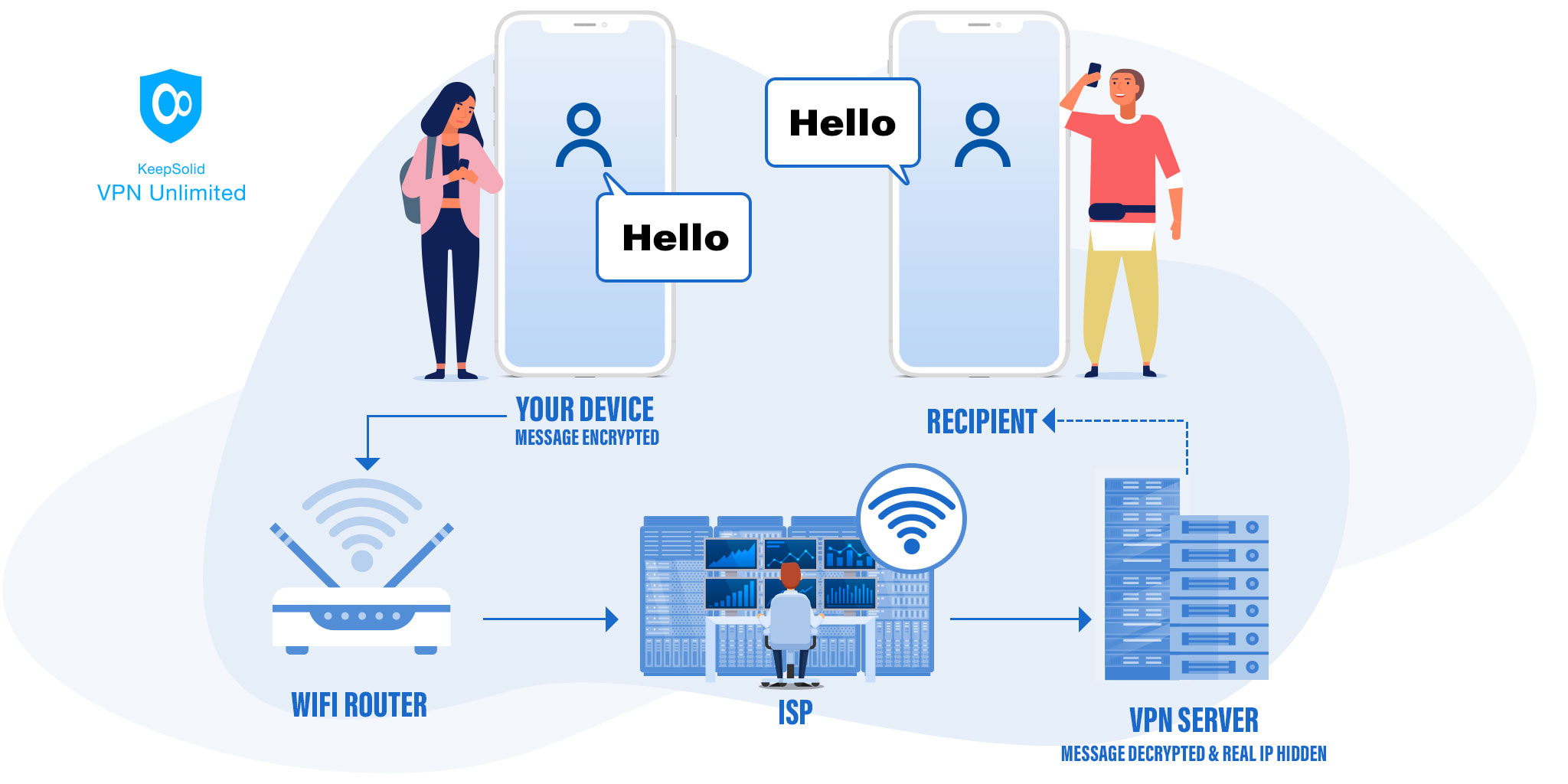
Without a VPN, here’s what happens when you enter a website URL in a browser:
- Your request travels from your device to your WiFi router
- The router sends the request to your ISP, a.k.a. Internet Service Provider
- The ISP directs the request to the website in question
- The website sends back the reply with the info you’ve requested, which then goes through all the previous steps in reverse
This procedure repeats multiple times until you leave the website. Unfortunately, it is quite unsecure, leaving multiple potential breach points that third parties can utilize. Namely:
- Your router can be hacked and infected with spyware, especially if it’s a public WiFi hotspot
- It’s not unheard of for ISPs to collect their clients’ personal information, including your IP address, location, online activities, interests, and habits
- The website might be collecting your data as well, or it can be compromised by malefactors and used for this purpose
Fixing these breaches is the essence of the VPN protection from hackers. To do this, a VPN establishes a secure tunnel between your device and the website. Your data travels through it, enciphered and hidden from prying eyes of any third parties, and your real IP address is masked. Neither ISPs nor other observers will get through this protection.
With a VPN, here’s what happens:
Can Hackers Get Through VPN?
It’s nice to know that VPN is a good security and privacy solution, but how reliable is it? Can a VPN be compromised and the encrypted data – hacked? Let’s analyze the efficiency of this solution at each step.
1. Does VPN Protect Your Device from Hackers?
As opposed to proxy servers, VPN ciphers all the inbound and outbound internet traffic of your device. For this, it uses the encryption technology. So even if someone taps into your connection and intercepts part of your traffic, they won’t be able to read it. To decipher it, they’d need your unique encryption key, and the only way to get that is by hacking your device.
Your device is easily the most vulnerable link in this chain. If it’s compromised, either because you’ve used a weak password, caught a virus, or fell for a social engineering attack, there’s nothing a VPN can do to safeguard you. It’s not that hackers can get through VPN – they got in before it had a chance to do something. So ensuring that your device is well-protected from such threats is vital.
2. Can Encrypted Data Be Hacked?
Now, let’s say your device is secure and you’ve enabled a VPN – how secure is your data once it’s ciphered by a virtual private network? As noted earlier, encrypted information can only be read using a special key. This key is located on two devices – your own and the VPN server you’re connected to. Your device encrypts the data, it’s transferred to the VPN server, which then deciphers it back and passes the now-readable data to the website.
The only way for a hacker to circumvent this procedure and steal your data is to brute-force the encryption protecting it. However, any modern decent VPN employs AES-256 encryption protocol to secure users’ traffic, which would take even the most powerful computer thousands of years to hack.
3. How to Secure Your IP Address from Hackers?
The next security node on the path of your traffic is the VPN server. Its protection depends on your VPN provider (or yourself, if you’re self-hosting a server) and the VPN protocol used.

The general rule of thumb is that free VPNs are usually less reliable in this regard than the paid ones – after all, installing top-notch security on VPN server is a costly endeavor. Besides, free VPNs are notorious for offering their services at no cost only to lure users in order to monitor and sell their sensitive information.
After receiving your encrypted message, the VPN server will decipher it and send the message to the end-website. This is where VPN data protection ends. But at the same time, this is how VPNs secures your IP address from hackers and helps you bypass content geo-restrictions.
Since all your traffic goes through a VPN server, anyone trying to trace it back will only get as much as the server’s IP. For any observer, it will seem like you are physically located in the VPN server’s vicinity. And if a piece of content is unavailable in your location, connecting to a foreign VPN server will solve this issue.
4. Is VPN’s Protection from Hackers Extended to Websites?
After your data is sent to the end-website by your VPN server, it’s once again unprotected out in the open. To see that your data is still secure even at this point, we highly recommend that you only visit websites that secure your connection.
How to tell one? Easy! Just take a look at the website’s URL – does it spell HTTP or HTTPS? If it’s the latter – congratulations, your connection is Secured (hence the S in the acronym). While not as strong as the encryption of a good VPN, it’s still better than nothing to ensure the integrity of your information.
Known Vulnerabilities and Leaks that Can Get VPN Compromised

Lastly, let’s talk about VPN vulnerabilities. Any system inevitably has its weaknesses. That doesn’t necessarily mean one should avoid such a system. Rather, they should stay aware of its flaws and know how to keep ahead of anyone who may wish to take advantage of them.
The most common risk to the VPN security is the risk of VPN leaks, especially IP leaks. It happens if a technology transfers the information of your real IP address in circumvention of the secure VPN tunnel. This doesn’t mean that malefactors can hack your VPN’s cipher – your data will still be intact. But the information about your physical location might become visible. To avoid this, you’d probably want to learn how to prevent WebRTC, DNS, and IPv6 leaks.